How Healthcare Software is Developed for HIPAA Compliance
This article will highlight HIPAA complaints, why it is needed and important, and also healthcare software development using HIPAA Compliance.

Are you looking for information on HIPAA compliance or the healthcare software developed using HIPAA compliance? If YES, this guide is for you. As per the statistics, more and more healthcare systems and organizations are turning towards online models like any other organization around the globe. The benefit of this is to reduce physical patient interaction. This concept showed more flow after the COVID-19 pandemic.
Software and apps related to healthcare are in great demand across the world. But taking healthcare virtual is a big deal as life and health are at stake. Here is where the HIPAA compliance role comes into play. Any developer, whether developing a health-related app or healthcare software, must comply with HIPAA compliance to launch.
What is HIPAA?
HIPAA stands for Health Insurance Portability and Accountability Act. It was first passed in 1996. The main reason for this act being passed is the software development companies for security and privacy rules for better patient management, confidentiality, and safety called PHI (patient-protected health information).

However, since the first emergence, various changes and updations have been made to HIPAA compliance as the technology improves and healthcare software threats occur.
HIPAA compliance software requirements
It is essential to know that healthcare software development must fulfill the following requirements to fulfill HIPAA compliance - Health Insurance Portability and Accountability Act. PHI (patient-protected health information) that is a must for HIPAA compliance are:
- Initials - (first, middle, and last name)
- Address
- ZIP code
- Date of birth
- Admission or discharge date
- Photographs
- Number (phone and fax)
- Biometric (fingerprints, two-factor authentication, and facial identification)
- SSN - Social Security Number
- MRN - Medical Records Number
- HPBN - Health Plan Beneficiary Number
- AN - Account Number
- License Number
- Device identifiers
- Website URLs and IP address
HIPAA compliance software checklist
For the successful software development of successful health-related software development and to guarantee its HIPAA compliance; the below-mentioned HIPAA compliance checklist is a must to follow:
Data access control
The first HIPAA compliance checklist is access control responsible for the permission of data usage. This can be prevented by roles-based access control and much more.
Activity audit
The next HIPAA compliance checklist is activity audit; healthcare software and app developers can secure and used only by relevant people and not everyone. This can be done by successful login, failed attempts, and stored information.
System integrity
The next on the HIPAA compliance checklist is the data and communication must be encrypted from end-to-end.
Anti tempering mechanism
Implementation of blockchain techniques and digital signatures can reduce security tempering in the health app or software.
Reliable user authorization
Security can be enhanced by techniques like keeping strong passwords, multi-step authentication, etc.
Safe data transmission
Ensure safe data transmission data must be regularly backed up through a trustworthy third-party facility.
How to become HIPAA compliant
To become a HIPAA-compliant app or software, the following are must:
Organization's privacy policy
The organization must create a privacy policy to become HIPAA compliant. Once created, it must be available as a Notice of Privacy Practices (NPP) and signed by the patients. This policy must cover the explanation of how the patient's privacy is addressed and inform their rights to them.
HIPAA privacy officer
HIPAA compliance is sometimes difficult to understand, so an organization should have its HIPAA privacy officers as an expert to head the creation of the company's privacy policies and ensure their implementation. The officer is also responsible for processing NPPs, organizing training sessions, and leading organizations' internal audits to ensure HIPAA compliance.
Regular internal audits
After getting approved for HIPAA compliance, a healthcare organization must get regular internal audits to recognize compliance voids. Healthcare organizations must then construct documented remediation strategies demonstrating ways to revert HIPAA infringements.
Preserve business contracts
Before sharing the data, ensure that the business associate is medical software HIPAA compliant, protects against data violation, and is revised to reminisce changes.
Infringement warning protocol
A HIPAA compliance infringement is not always an issue, especially if it's done accidentally and the organization can prove it.
Adequate documentation
Healthcare organizations must report and document all HIPAA compliance measures. These medical records will be inspected for audits and complaint analyses.
The HIPAA privacy rule
It requires healthcare software solution users' rights on their confidential data, called protected health information - PHI, and must be kept private. The information includes a patient's current medical issues, previous issues, treatment history, transaction history, etc. It summarizes how the data will be used and who can access it. The patient has the right to access their data and get it copied. The organization's privacy policy must be written, documented, and informed to the patient.
The HIPAA security rule
Organizations are required to secure protected health information - PHI under the HIPAA Security Rule. The HIPPA Security Rule explains how to proceed. More precisely, the Security Rule establishes international standards for the handling, maintaining, and transmitting of electronically protected health information (ePHI).
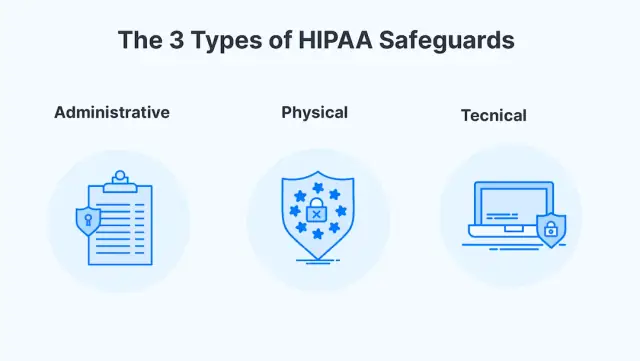
Administrative, physical, and technical protections are the data security measures that must be in place for the healthcare industry to comply with this guideline.
Administrative safeguard
According to administrative safeguards, it is compulsory for entities working with protected health information - PHI to assign a trustworthy officer and organize a security management system to record all the information safely. Security rules also include employee training, management, and evaluation of security policies. Make sure you hire an officer eligible to sense cyberattacks and work on them promptly to save the internal information of your hospital. It protects your data from sharing with any third party and unauthorized department. With HIPPA-compliant app rules, the officer has to predict the risks and manage to overcome them on time.
Physical safeguard
This safeguard provides physical storage in a remote center or electronically protected health information - ePHI stored on-premise in the cloud. If you are accessing electronically protected health information - ePHI from your device, you must follow the security policies, such as deleting the electronically protected health information - ePHI from your device after ending the contract. Secure workstations Your workstations with ePHI access must have a tight security system, including proper door and window locks and video inspection to ensure that computers and servers are safe.
Technical safeguards
This safeguard includes the technologies related to transmission integrity, and the audit is secure. Must have permit towards secure PHI databases to ensure workers only access the authorized data and not all. It must be end-to-end encrypted. The created email for transmission must be secure as per medical software HIPAA Compliant Messaging solutions.
This technology security is for damage control in case of a power cut, restarting or updating the system, or any incident that may cause an error. It ensured the data and recovered to the entities in the correct shape. Plus, it only provides authorized users unique access to the relevant department. All the information is accessed only with biometrics, smart cards, or passwords.
HIPAA-compliant software development
To develop a healthcare software solution or app, you must ensure it is within HIPAA compliance to protect the patient's information. Because if you don't comply and follow along with HIPAA can result in serious outcomes. Many health organizations pay fines due to privacy breaches in HIPAA. So making an online healthcare organization takes much more than just building an app or medical software solution. You must uphold the confidentiality, privacy, and virtue of your electronic PHI on the app.
AppMaster offers HIPAA-compliant healthcare software solutions and app development using no-code technology. Here at AppMaster, we ensure that your product is per HIPAA compliance so that these devastating data breaches do not happen.
How to build HIPAA-compliant software systems
Suppose you want to build your HIPAA-compliant healthcare system from the start. In that case, it will depend on the functions you want to include and the main purpose behind developing the HIPAA compliant app called the hospital management system (HMS).
HMS is a great tool that will provide working ease for doctors, nurses, and medical staff whenever they want to access the data while maintaining the patient's privacy and data security. The general rules to develop the HMS are:
- It should be extended to every medical worker.
- UI/UX design must be admiringly enlightening.
- It must contain user access control.
- It contains a reliable security system.
- Data can be stored regularly on third-party platforms.
- Data must be end-to-end encrypted.
- The HMS medical software solution or app must be able to deliver betterment for clinic automation.
- The healthcare software development must be HIPAA compliant.
- The cost of software development must be reasonable.
The software development crucial for the HIPAA-compliant software system or a healthcare app can be done easily through a no-code technology. Consider AppMaster the best platform to get your mobile app or web application for any purpose. The healthcare management software development or app can also be created by a traditional coding method by healthcare software developers, but working your way towards AppMaster, a no-code platform, is easy to use, cost-effective, user-friendly, and consumes less time. AppMaster ensures that the app you created from the platform follows all the HIPAA compliance requirements mentioned above:
Transport encryption
Before transmission, all electronic PHI should be encrypted. The first step in securing sensitive health information with SSL and HTTPS protocols is ensuring that HIPAA-compliant software encrypts it during transmission. Verifying that the HTTPS protocol is configured correctly and that no outdated or unsafe TLS versions are present is advised.
Backup and storage
Data backup must be ensured, kept, and only accessible by authorized staff. Ensure only authorized individuals have access to sensitive PHI, including logs, backups, databases, and all data your system keeps. It is possible to keep it in locations out of your control, for example, on the same hosting plan but using a shared server with multiple customers. No matter what, the data should be encrypted and inaccessible at any cost.
System logs and identity
Regarding system logs, IDs and passwords must be as secure. HIPAA compliant software has very rigid criteria about the level of privacy to be maintained. The system should be able to track all the logs and modifications constructed to PHI. The key factors are:
- Strong password
- Limit login attempts
- Two-factor authentication (2FA)
- Multimodal biometrics - fingerprint, face, or voice recognition
- Single sign-on (SSO)
- Liveness detection
- Attribute-Based Access Control
Blockchain
It can help with the health management system (HMS) through the following:
- Semi-trusted third parties can be avoided
- Evolved cryptographic encryptions that prevent hacking
- Pseudonymity to protect user identity
- Modifying block records
- Secure the data rights of patients
- Competitive corporations of medical assistance and analysis
- Transactions will be recorded
- More trustworthy
- Data transparency
Disposal
To maintain health data security and HIPAA compliance, backed-up and archived data should expire and permanently be discarded. When someone is no longer using the server, ensure data is disposed of from every location where the data is transferred because it might have to make backups or copy it.
Business agreement
The HIPAA compliant software systems and electronic PHI must be hosted on the company's servers with a signed Business Associate Agreement or at least have a secure in-house server. The best options among the most trusted providers are
- Google Cloud Platform
- Amazon Web Services
- Microsoft Azure
How to maintain HIPAA compliance - AppMaster's Experience
Building the HIPPA compliance app or software is another thing, but maintenance is always needed. The conclusion in maintaining HIPAA compliance is attentiveness and checking, but the manual methods of doing so will be time taking and not cost-friendly. The advanced AI technology will allow doing that effectively via automatically searching the patient's information, Automated scanning to reduce risk, and instant data recovery through regular backups. For the maintenance of HIPAA compliant software with your custom healthcare software applications, let us quote you the AppMaster experience and how it is done.
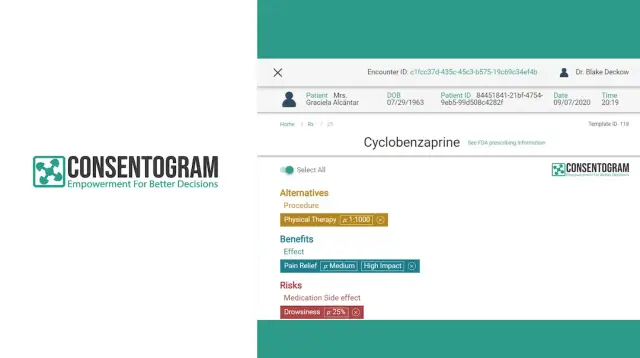
Consentogram is a type of automatically informed consent method. This was the AppMaster's resolution towards the ePHI that delivers seamless integration toward electronic data storage, maintenance of pre-existing information, and reduces manual workflow.
This piece of the invention was created on an artificial intelligence model and works of clinical decision support (CDS), plus ML-based malpractice risk reduction for healthcare providers. On AppMaster, the backend of Сonsentogram was developed and then incorporated with the ePHI systems of healthcare setups and work on the protocols of HIPAA and HITECH. AppMaster's collaboration on the project was time-effective and cost-effective, with successful maintenance offered at intervals. Learn more about Consentogram on AppMaster.
The bottom line
To build your health management system or a healthcare-related software or app, you must make sure that it ensures all the HIPAA compliance recommendations. Without doing so, the healthcare software or app will not be valid for longer and will not meet the required safety and patient privacy protocols. By implementing HIPAA compliance and making an app or software that fulfills all the safety protocols, fraud, identity thefts, hacking, or personal information breaches will be minimum. This will also protect your healthcare organization from getting avoidable financial fines from the governing bodies.
If you want to build your healthcare app or backend, AppMaster can help you with that. It has a powerful visual programming tool and backend for a healthcare-related app if you ensure that your app fulfills the required HIPAA compliance protocols during software development. Check out the reasonable packages and get started with your app today!





