How Software Architecture Impacts Cybersecurity
Best practices, patterns, and strategies to enhance cybersecurity in your software.

Importance of Software Architecture in Cybersecurity
Software architecture is essential to designing, developing, and implementing computer systems and applications. It provides a blueprint for defining the structure, relationships, and interactions of various components within a system. In terms of cybersecurity, software architecture plays a critical role in preventing security breaches, safeguarding sensitive data, and ensuring the stability and integrity of an application.
One of the core objectives of good software architecture is to establish a solid foundation for system security. By taking a proactive approach to address security concerns during the initial design and development phase, organizations can minimize the risk of vulnerabilities that potential attackers can exploit.
Furthermore, a well-structured architecture facilitates the implementation of security countermeasures and makes monitoring and safeguarding the system's components easier against future threats. Inadequate software architecture can lead to severe consequences, such as data breaches, system downtime, or even legal liabilities.
Therefore, developers and architects must prioritize security when designing and building applications. By incorporating security measures from the outset and adhering to best practices, organizations can greatly reduce the likelihood of security incidents and protect their valuable assets in an increasingly cyber-threatened world.
Understanding Layers and Their Security Implications
Modern software applications can be complex and are often built on multiple layers. Each layer plays a specific role in the system's operation, and understanding the security implications of these layers is vital for safeguarding your applications. Let's examine some common layers in software architectures and their associated security challenges.
- Presentation Layer: This is the user-facing layer of your application, responsible for displaying information and facilitating user interactions. Security challenges at this layer include cross-site scripting (XSS), clickjacking, and insecure user input handling. To secure the presentation layer, implement proper input validation, output encoding, and employ secure mechanisms for handling cookies and session data.
- Application Layer: A crucial layer that contains the business logic and processes user requests. Common security risks at this layer include authentication and authorization flaws, insecure access controls, and business logic vulnerabilities. To secure the application layer, adhere to secure coding practices, implement strong authentication mechanisms, and follow the principle of least privilege.
- Data Access Layer: This layer focuses on data storage and retrieval, often interacting with databases and other storage systems. Security challenges in the data access layer include SQL injection, data leaks, and unauthorized access to sensitive information. To protect this layer, use parameterized queries, data encryption, and apply strict access controls.
- Networking Layer: The layer responsible for facilitating communication between different systems or components in a distributed application. Common security challenges include man-in-the-middle attacks, denial of service (DoS), and insufficient transport-layer security. To secure the networking layer, use encrypted communication channels, ensure proper authentication and authorization, and deploy firewalls and intrusion detection systems.

By understanding the security implications of each layer, architects and developers can adopt specific strategies to address vulnerabilities and protect their applications from a wide range of attack vectors.
Secure Coding Practices for Better Cybersecurity
Secure coding practices are essential for building secure and reliable applications that can resist potential attackers. Here are some fundamental secure coding practices that developers should follow to improve application security:
- Validate and Sanitize User Input: User input can be a primary source of security vulnerabilities if improperly handled. Stray input errors can lead to SQL injection, XSS, or other types of attacks. Developers must rigorously validate and sanitize user inputs to eliminate potential threats before the application processes the input.
- Use Parameterized Queries: SQL injection attacks are prevalent and can lead to unauthorized data access or manipulation. Using parameterized queries can help mitigate SQL injection risks by correctly separating user input from SQL commands, preventing attackers from injecting malicious code.
- Implement Strong Authentication and Authorization: Proper authentication and authorization mechanisms ensure that only legitimate users access your application's resources. Implement multi-factor authentication (MFA), use strong password policies, and follow the principle of least privilege to minimize unauthorized access risks.
- Use Encryption and Secure Communication Protocols: Data encryption protects sensitive data at rest and in transit. Utilize secure communication protocols like HTTPS and TLS, and encrypt sensitive data stored in databases or other storage systems.
- Keep Third-Party Libraries and Dependencies Up to Date: Outdated or vulnerable third-party libraries can expose your application to security risks. Regularly update your dependencies and rigorously test them for potential vulnerabilities.
- Perform Regular Security Testing: Regular security testing activities, such as static analysis, dynamic analysis, and penetration testing, can help detect and address vulnerabilities before attackers can exploit them.
Adopting secure coding practices is a crucial aspect of ensuring application security. By following established industry best practices and continuously improving their development processes, organizations can create more secure applications and reduce the risk of cybersecurity incidents.
Architectural Patterns for Enhancing Security
Software architecture is critical in establishing and maintaining a system's security. Developers can create secure applications by design by employing effective architectural patterns, thereby reducing vulnerabilities and potential attack vectors. In this section, we will explore some common architectural patterns that help enhance security in software systems.
Defense-in-Depth
Defense-in-Depth is an approach that layers multiple security mechanisms to protect a system. It is based on the principle that if one security mechanism fails, others still provide protection. Defense-in-Depth can be employed at various levels, such as network, host, application, and data. Combining multiple security barriers makes it more challenging for attackers to exploit vulnerabilities and infiltrate a system. Implementing Defense-in-Depth can involve various practices, such as:
- Using firewalls and intrusion detection systems (IDS) to protect the network
- Employing strong authentication and access control mechanisms
- Securing communication channels using encryption
- Applying secure coding practices and rigorous testing to eliminate software vulnerabilities
- Protecting sensitive data with encryption and secure storage solutions
Principle of Least Privilege
The Principle of Least Privilege states that a user, process, or system should only have the minimum necessary permissions to perform their tasks. This approach minimizes potential damage caused by compromised accounts or software vulnerabilities, as attackers have limited permissions to leverage. To implement the Principle of Least Privilege, developers should:
- Assign permissions based on roles, with each role having the least privilege necessary
- Limit the use of administrative accounts to specific tasks that require elevated privileges
- Regularly review and update permissions to ensure they remain aligned with job requirements
- Implement strict control over shared resources, such as file systems, databases, and network connections
Separation of Concerns
Separation of Concerns is a design principle that advocates for partitioning a system into distinct components with specific responsibilities. This approach helps minimize the impact of vulnerabilities by isolating and containing potential breaches within individual components. By employing Separation of Concerns, developers can:
- Create isolated execution environments to prevent unauthorized access or manipulation of system components
- Improve maintainability and decrease the likelihood of vulnerabilities by reducing component interdependencies
- Make it easier to enforce security policies at a component level, which can simplify access control and auditing
- Enhance system resilience by preventing the propagation of failures or compromised components across the entire system
Secure by Design
Secure by Design is an approach that aims to build security into the software architecture from the ground up. Instead of treating security as an afterthought or add-on feature, Secure by Design ensures that security is integral to the development process. To adopt Secure by Design, organizations can:
- Develop a thorough understanding of potential threats and risks, and incorporate security requirements into the development process
- Engage security experts early in the development lifecycle to assess and refine the software architecture
- Conduct continuous security reviews and assessments throughout the development process
- Implement secure coding practices, automated testing, and vulnerability scanning to identify and rectify security vulnerabilities proactively
Monitoring and Logging Strategies for Security
Effective monitoring and logging strategies are vital to maintain and improve application security. By collecting and analyzing application behavior data, developers can detect potential security threats and respond to incidents more effectively.
Real-Time Threat Detection
Monitoring applications in real-time allows for immediate detection of security anomalies. By continuously tracking user activity, system performance, and network traffic, organizations can identify potential threats and take action before they escalate into more serious incidents.
Analyzing System Behavior
System behavior analysis is crucial in understanding normal and anomalous activity patterns. Organizations can identify trends and detect deviations that might indicate a security breach or vulnerability by gathering data from various sources, such as log files and performance metrics.
Incident Response and Remediation
When a security threat is detected, having a well-defined incident response plan helps organizations react swiftly to contain and remediate the threat. Monitoring and logging data can be invaluable during incident response, as it provides important information about the attack, potential vulnerabilities, and any changes made to the affected systems.
Auditing and Compliance
In many industries, adhering to security standards and compliance requirements is essential. Monitoring and logging enable organizations to track their adherence to these standards and provide evidence of compliance during audits. This can also help identify areas where improvements are needed and foster a culture of continuous security improvement.
Integrating Security Tools into the Development Lifecycle
To build and maintain secure software systems, it is essential to integrate security tools and processes throughout the development lifecycle. By doing so, organizations can proactively identify and address potential vulnerabilities, reduce the risk of costly security breaches, and ensure continuous security improvement.
Static and Dynamic Security Testing
Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) are essential for identifying potential vulnerabilities in the source code and during runtime. Integrating these security testing tools early in development can help developers address vulnerabilities before deploying the software.
Dependency and Vulnerability Scanning
Modern applications often rely on third-party libraries, frameworks, and components. To minimize the risks associated with these dependencies, developers should use tools that scan and evaluate dependencies for known vulnerabilities. Integrating dependency and vulnerability scanning tools enables organizations to stay up-to-date on security vulnerabilities and apply necessary patches and updates.
Continuous Integration and Continuous Delivery (CI/CD)
Automated CI/CD pipelines can help organizations maintain a high level of security by incorporating security checks and tests throughout the deployment process. CI/CD pipelines can be configured to fail if security vulnerabilities are detected, allowing developers to fix issues before they reach production.
Security Information and Event Management (SIEM)
SIEM tools collect, correlate, and analyze log data from various sources to detect and respond to security incidents. Integrating SIEM solutions into the development lifecycle can help organizations gain a comprehensive view of their security posture and streamline their incident response process.
One way to ensure that your applications are built with security in mind is to utilize no-code and low-code platforms like AppMaster. These platforms have built-in security best practices, features, and architectural patterns that help developers create secure applications more quickly and cost-effectively. Moreover, by reducing manual coding, these platforms can help eliminate potential vulnerabilities associated with human error.
Using No-Code and Low-Code Platforms for Secure Applications
As the demand for secure applications grows, no-code and low-code platforms have emerged as viable solutions to streamline the development process while maintaining a strong focus on security. These platforms enable developers and non-technical users to create applications quickly and cost-effectively, without the need for extensive coding skills. Moreover, they often incorporate built-in security features, best practices, and architectural patterns to minimize potential vulnerabilities and reduce the risk of cybersecurity breaches.
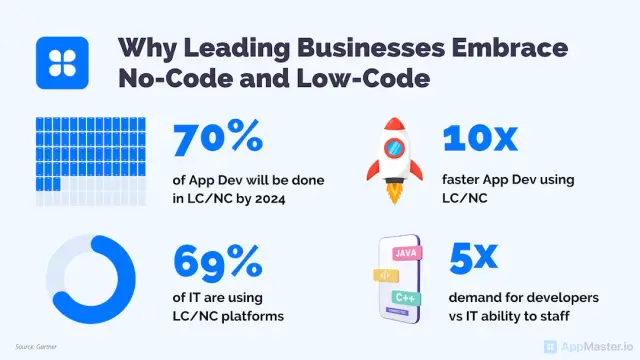
Advantages of No-Code and Low-Code Platforms for Cybersecurity
There are several key advantages to using no-code and low-code platforms for developing secure applications:
- Built-in Security Features: No-code and low-code platforms often provide out-of-the-box security features such as data encryption, user authentication, and access control. This enables organizations to easily enforce security best practices across their entire application portfolio.
- Faster Development Cycles: By significantly reducing the amount of manual coding required, no-code and low-code platforms enable faster development cycles. This accelerates time-to-market and allows for more frequent software updates, making it easier to address security vulnerabilities and maintain up-to-date applications.
- Reduced Human Error: Manual coding can be prone to human error, introducing potential vulnerabilities into the application. With no-code and low-code tools, many of these opportunities for error are eliminated, resulting in more secure applications.
- Emphasis on Security Best Practices: No-code and low-code platforms are designed with security in mind, often encapsulating industry-standard security best practices and architectural patterns within the platform itself. This helps ensure that applications being developed are secure by default.
- Accessible to Non-Technical Users: No-code and low-code platforms enable non-technical users, such as business analysts and subject matter experts, to contribute to the development process. This can help infuse a security-aware mindset throughout the organization and encourage cross-functional collaboration on security matters.
AppMaster: A No-Code Platform with a Focus on Security
AppMaster is a powerful no-code platform allowing developers and non-developers alike to visually create backend, web, and mobile applications. With its focus on security, AppMaster provides several key features that help ensure the cybersecurity of the applications built using the platform:
- Visual Data Modeling: AppMaster allows users to create data models (database schema) visually, helping to enforce data security best practices and reduce potential vulnerabilities associated with manual coding.
- Business Logic Design: With its visual Business Process (BP) Designer, AppMaster enables users to define and implement the business logic for their applications, ensuring that security measures are consistently enforced throughout the entire system.
- REST API and Websocket Secure Endpoints: AppMaster generates secure REST API and WSS endpoints for applications, facilitating secure communication between applications and backend systems.
- Scalable and High-performance Applications: Applications generated by AppMaster are compiled and stateless, resulting in highly scalable and performance-efficient solutions that support enterprise and high-load use cases.
- Elimination of Technical Debt: As AppMaster regenerates applications from scratch whenever requirements are modified, technical debt is virtually eliminated, helping to maintain a high level of application security over time.
Organizations can build secure applications more efficiently by using a no-code platform like AppMaster, benefiting from industry-leading security features and best practices. As a result, they can devote more time and resources to continuous improvement, further strengthening their cybersecurity posture and protecting their most valuable digital assets.
FAQ
Software architecture plays a crucial role in defining the structure, relationships, and interactions of various components in a system. It directly affects cybersecurity by addressing foundational security issues, such as data protection, access control, and user authentication.
Secure coding practices help developers write code that is less prone to vulnerabilities, making it harder for attackers to exploit. Benefits include reduced risk of data breaches, legal liabilities, and reputational damage, as well as improved user trust and compliance with industry standards.
Common architectural patterns for enhancing security include Defense-in-Depth, Principle of Least Privilege, Separation of Concerns, and Secure by Design. These patterns help protect data, enforce access control, and minimize the attack surface of an application.
Monitoring and logging enable organizations to detect security threats in real time, analyze system behavior, and quickly respond to potential breaches. They provide the necessary information for identifying vulnerabilities, tracking user actions, and understanding the impact of an attack.
Integrating security tools into the development lifecycle ensures that security is considered from the beginning of the project. It helps identify and address potential vulnerabilities early on, reducing the risk of costly security breaches and promoting a culture of continuous security improvement.
No-code and low-code platforms, like AppMaster, enable developers to build secure applications faster and more cost-effectively, as they often come with built-in security features, best practices, and architecture patterns. They can help reduce human error and eliminate potential vulnerabilities associated with manual coding.





