What is Endpoint Security?
Endpoint security has become essential for all organizations to deal with the increasing number of cyberattacks. Learn all about endpoint security here.

Nowadays, businesses and individuals rely on a wide range of endpoint systems like mobile devices, tablets, laptops, PCs, smart TVs, and smartwatches to perform different functions. All of these IT devices, systems, and networks are vulnerable to cyberattacks.
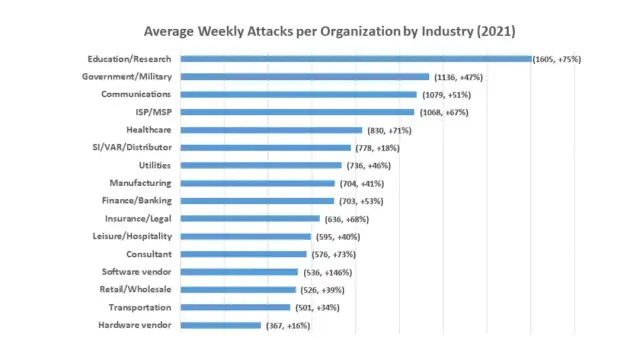
In fact, the statistics indicate that the number of cyberattacks has greatly increased in the last few years. Since every device that is being connected to a business network is vulnerable to attacks that cybercriminals can carry out to steal or exploit sensitive data, it is important to implement thorough endpoint security measures. In this article, you will get to know about all the critical aspects of endpoint security, how it works, and the importance of endpoint security solutions.
What is endpoint security?
Endpoint security is the process of securing endpoints (entry points) of end-user systems. An endpoint is any device that connects to a network from outside of its firewall. Some of the popular examples of endpoint systems are laptops, desktops, smartphones, point-of-sale systems, digital printers, and several other internets of things (IoT) devices.
The primary goal of an endpoint security solution is to safeguard the entry points of IT systems from getting exploited by malicious attacks by hackers and other cyber threats. Using an efficient endpoint security platform, make sure that the endpoints are protected in a conventional system as well as modern cloud-based systems.
You can also think of the endpoint security platforms as an advanced version of conventional security software. Modern endpoint security measures provide comprehensive protection from complex malware and cyber threats to secure the systems and guard the company's information.
It is important to note that all types of organizations, businesses, and personal systems are at risk of facing cyberattacks. Therefore, endpoint security is considered to be the frontline security mechanism in cybersecurity. Companies that want to make their systems and enterprise networks safe and secure should start by implementing reliable endpoint security solutions.
What is the importance of endpoint security?
The increasing volume and sophistication of IT security threats have made endpoint security much more important than ever before. Modern endpoint security platforms are designed to quickly detect, analyze, and block attacks. As a result, companies have to focus on the implementation of endpoint security solutions to deal with various cyber threats.
Moreover, data is the currency of the digital era. Every small business, as well as a multinational corporate industry, has to protect sensitive information from numerous hackers and cyber threats. Large-scale cyber threats have the potential to put an entire business at risk of financial bankruptcy and a massive public scandal.
A significant reason behind the increasing number of cyber threats is the fact that the number of types of endpoints in an organization has also increased. Nowadays, a company has different smart systems such as mobile devices, desktops, laptops, tablets, smart speakers, smart TVs, and many other interconnected devices through which hackers can penetrate a well-integrated IT system.
As a result, implementing cybersecurity policies has become essential for businesses. It is also important to keep these tools and policies up-to-date, as hackers are also coming up with new ways to manipulate businesses and gain sensitive data.
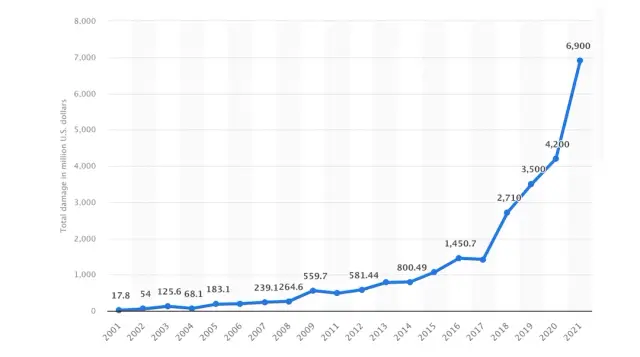
The following graph shows the total reported financial damages caused by cybercrimes. It is evident that the losses sharply increased in 2020, which proves the increasing number and complexity of cyber threats.
Components of endpoint security
There are certain common components of endpoint protection platforms to ensure maximum endpoint security. These features and components work together to provide the best protection and make sure an organization is able to benefit from reliable endpoint security measures.
These essential components of the endpoint protection platforms are:
- Centralized endpoint management platform to deal with endpoint security issues from the same platform.
- Advanced anti-malware protection to detect and correct viruses and malware.
- Proactive web security to ensure endpoint security in different types of devices connected to a company's IT infrastructure.
- Data loss prevention and recovery is also a significant part of major endpoint protection platforms.
- Endpoint security of modern ML and AI-based systems.
- Integrated firewall.
- Cyberattacks via emails and social media messages are also common, so endpoint protection platforms provide endpoint security measures to deal with them as well.
- Insider threat protection to ensure endpoint security from within a company.
What is an endpoint security example?
There are many different examples of endpoint security, such as security software and web filtering. You can better understand endpoint security by getting familiar with its types and core functionalities of endpoint protection strategies:
Endpoint Protection Platform
In order to achieve point-in-time protection, an EPP solution inspects and scans information as soon as they reach a system. A traditional antivirus (AV) solution is the most popular kind of endpoint security. Anti-malware features included in an AV system are primarily meant to protect against attacks using signatures. An AV program scans each file that enters your network to see if its signature matches any dangerous threats in a threat intelligence database.
Endpoint Detection and Remediation
An EDR solution goes farther than simple point-in-time detection systems. Instead, it keeps track of all files and programs that are downloaded into a device. As a result, EDR solutions may provide threat research with finer-grained visibility and analysis. EDR solutions can identify risks that go beyond attacks that use signatures. EDR solutions can find file-less malware, ransomware, polymorphic attacks, and more.
Extended Detection and Response
In areas where EDR outperforms conventional security capabilities of detecting malware, XDR broadens the scope of endpoint protection to include more widely used security solutions. XDR is more versatile than EDR. It makes use of up-to-date technology to increase visibility, gathers threat data, correlates it, and uses analytics and automation to find existing and upcoming attacks. The goal of EDR is to perform quick detection and response to the cyberattack.
Threat Intelligence Integration
Businesses must be aware of dangers as they change if they want to remain one step ahead of attackers. Security teams need current and accurate information to make sure defenses are automatically and accurately calibrated since sophisticated adversaries and advanced persistent threats (APTs) may move rapidly and covertly.
To examine every occurrence and learn more in minutes rather than hours, a threat intelligence integration solution should include automation. In order to provide proactive protection against upcoming attacks, it should produce unique indicators of compromise (IoCs) straight from the endpoints. There should also be a human component made up of knowledgeable security researchers, threat analysts, cultural specialists, and linguists who can understand new risks in various circumstances.
How does endpoint security work?
In order to protect endpoints, including servers, workstations, mobile devices, and workloads, from cybersecurity threats, companies deploy centrally managed security solutions known as endpoint protection platforms (EPP) or endpoint security solutions. Endpoint solutions search for signs of suspicious or malicious activities in files, processes, and system activity and deal with them to ensure maximum endpoint security.
The purpose of EPPs is to provide a centralized management dashboard from which administrators may access their company's network in order to watch over it, safeguard it, look into it, and deal with issues. By using an on-premises, hybrid, or cloud strategy for endpoint protection, the desired goal of ensuring maximum endpoint security is achieved. The working of endpoint security can be understood in a better way by categorizing it into three different approaches:
Traditional Approach
When referring to an on-premise security posture that depends on a locally hosted data center from which security is supplied, the term "Traditional or legacy" is often used. The management console connects to the endpoints via an agent in the data center to offer security. Due to the fact that administrators often can only monitor endpoints within their perimeter, this kind of approach is typically not preferred by most companies.
Hybrid Approach
Many firms have switched to laptops and bring your own device (BYOD) instead of desktop systems as a result of the pandemic-driven movement toward working from home. The constraints of the on-premise strategy are highlighted by this as well as the globalization of workforces.
In order to get certain cloud features, several endpoint solution companies have switched to a "Hybrid" strategy in recent years. It involves taking the legacy architectural design and modifying it for the cloud per a company's specific requirements.
Cloud-Based Approach
The cloud-native or cloud-based endpoint security solution is meant to safeguard the entire cloud system. It involves using a centralized management console that is present within the cloud and connects to connected systems remotely through an agent on the endpoint.
Administrators can monitor and manage endpoints remotely and perform diagnosis and security analysis at any time from anywhere. These solutions use cloud-based controls and policies to remove security issues and extend administrator reach while maximizing security performance outside of the conventional boundary of an organization.
Is endpoint security an antivirus?
Whether endpoints are real or virtual, on-premises or off, located in data centers or the cloud, endpoint security software guards against breaches. It is set up on distant endpoints like desktops, laptops, servers, virtual machines, and so on.
One of the most fundamental types of endpoint protection, antivirus, is often included in endpoint security solutions. AV program merely discovers and deletes known viruses and other forms of malware, as opposed to using more sophisticated methods and tactics like threat hunting and endpoint detection and response (EDR).
Typical security software operates in the background, regularly analyzing the content of a device for patterns that match viral signatures stored in a database. Both within and outside the firewall, individual devices have antivirus software installed. In simpler words, AV is one part of an entire endpoint security solution. Following are the three major differences between them:
Network security
Antivirus programs are intended to safeguard a single endpoint by providing insight into and, often, access to just that endpoint. The business network is instead seen as a whole by the endpoint security software, which also provides visibility of all linked endpoints from the same place to ensure maximum network security.
Hackers are using increasingly advanced attack techniques to find new ways to infiltrate corporate systems, steal data, and coerce workers into disclosing private information. The modern organization must be secured in order to keep hackers out of its IT infrastructure, which depends on endpoint protection.
Management
Antivirus solutions involve manually updating the databases or permitting updates from time to time. Endpoint security platforms, especially cloud-based solutions, provide integrated security that transfers security duties to an organization's IT staff. It makes the entire process of implementing endpoint protection protocols quick and easy.
Level of protection
Traditional AV solutions search for viruses and malware using signature-based detection. It means that you might face cybersecurity risks if your company was the first one to face a new threat or your AV was not up-to-date.
The latest EPP solutions are automatically maintained up to date by using the cloud to protect the devices and provide network security. Additionally, by using technologies like behavioral analysis, previously unknown risks can be dealt with through an efficient endpoint security solution.
The conventional method of securing the company perimeter through antivirus is no longer practical since workers access systems through different systems and from multiple networks, and from various places. Modern endpoint protection measures are critical to providing maximum endpoint security.
No matter how or where workers connect to corporate data and resources, endpoint security guarantees that the company puts security on its systems, allowing them to do so in a secure manner. Endpoint security solutions provide a reliable and efficient method of ensuring maximum security.
Security of apps in a no-code development approach
No-code development approach has become highly popular. A study showed that only 0.5% of the world's population is good at coding, while 85% of people who participated in a survey said that no-code tools add great value to their lives.
Since security is a critical part of development, AppMaster, the most efficient and powerful no-code development tool, has put special attention on ensuring maximum safety while following the no-code development approach. It provides a safe and secure development environment to defend your privacy through comprehensive logging and using state-of-the-art AWS data separation measures.
Conclusion
The bottom line is that endpoint security is a vital part of any business. Using endpoint protection platforms has become a necessity in the digital era to prevent cyberattacks and massive losses caused by different types of cybercrimes.
As workers increasingly connect through different types of devices and an increasing number of endpoints, businesses need to take security precautions. Additionally, they must guarantee that the data stored on such systems are safe and cannot be stolen or lost.
A lot of companies have shifted to a remote working model, which means a wide range of endpoints is connected to an organization. Cloud-based endpoint security solutions are useful in such situations to prevent all types of cyberattacks.





